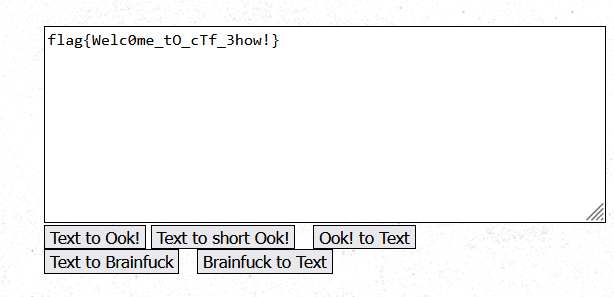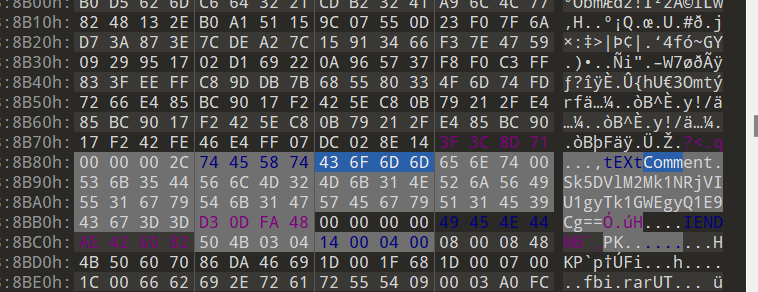
丢进010在文件中部找到密文
Sk5DVlM2Mk1NRjVIU1gyTk1GWEgyQ1E9Cg==
|
base64解码,在base32解码
图片大小过大,用binwalk查看
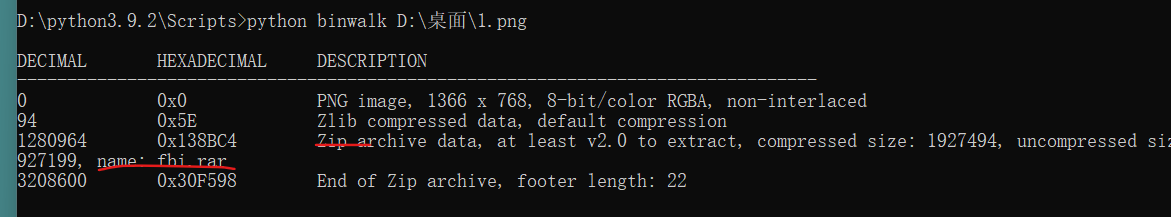
binwalk -e分离文件得到flag.zip
我的解压软件看不到提示,直接跑出zip密码:123456
thienc.txt里的3078就是十六进制中的0x
python脚本将thienc.txt转为十六进制文本
import re
def read_file(filepath):
with open(filepath) as fp:
content=fp.read();
return content
number = read_file('thienc.txt')
result = []
result.append(re.findall(r'.{2}', number))
result = result[0]
strings =''
for i in result:
y = bytearray.fromhex(i)
z = str(y)
z= re.findall("b'(.*?)'",z)[0]
strings += z
b= strings.split('0x')
strings=''
for i in b:
if len(i) ==1:
i= '0' + i
strings +=i
with open('result.txt', 'w') as f:
f.write(strings)
print("complete!")
|
得到文本
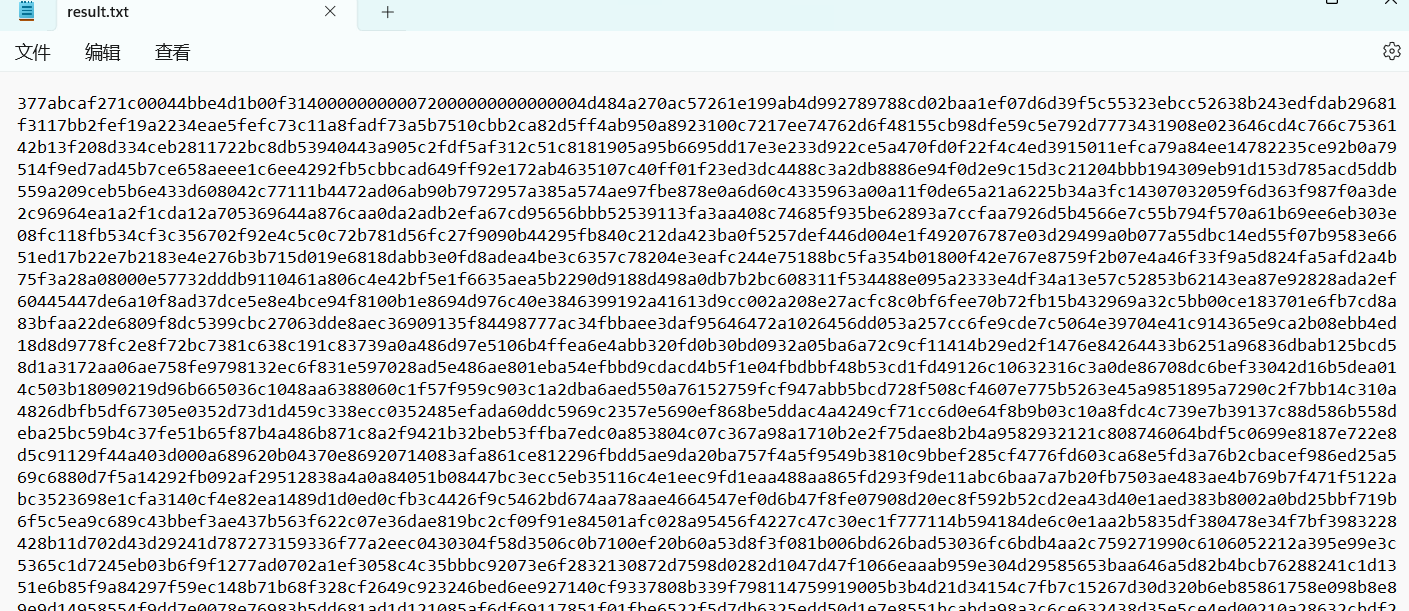
注意到37 7A BC AF是7z格式压缩文件的文件头
复制文本粘贴进010(ctrl+shift+v),将文件后缀保存为7z
得到一个加密的文档, 结合之前得到的key 解压得到secenc.txt
很明显为base64编码,但解码不对
发现这段字符串经过了多重的base64和base32混合编码。循环用正则表达式匹配判断编码类型然后解码: 脚本为
import base64
import re
f = open('secenc.txt').read().encode('utf-8')
while True:
if re.match('^[2-7A-Z=]+$', f.decode('utf-8')):
f = base64.b32decode(f)
elif re.match('^[0-9a-zA-Z+/=]+$', f.decode('utf-8')):
f = base64.b64decode(f)
else:
print(f.decode('utf-8'))
break
with open('result1.txt', 'w', encoding='utf-8') as file:
file.write(str(f,encoding='utf-8'))
print("Decryption complete!")
|
输出结果:
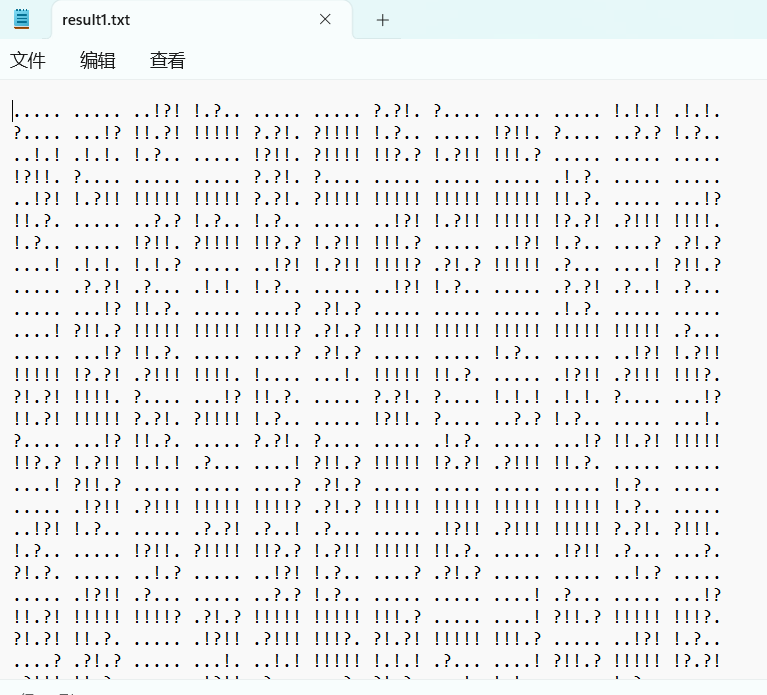
ook编码,解码得到
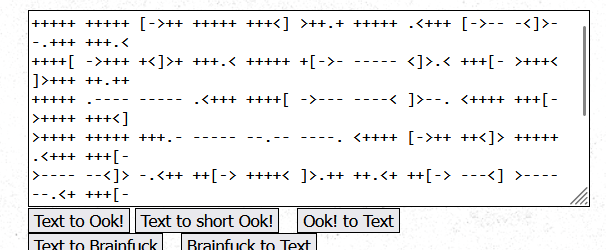
brainfuck –>text运行得到: